Trézór Bridge®™ | Secure Crypto Connectivity
Introduction: A Foundation for Trusted Crypto Access
In the rapidly evolving digital asset ecosystem, security and reliability are not optional features—they are absolute necessities. Hardware wallets have become the gold standard for safeguarding cryptocurrencies, and within this ecosystem, Trezor stands as a pioneer. At the core of its secure communication framework lies Trezor Bridge, a lightweight yet powerful connectivity layer designed to ensure safe interaction between Trezor hardware wallets and desktop environments.
Trézór Bridge®™ is not just background software; it is a critical security component that enables encrypted, authenticated communication between your physical wallet and supported applications. Without it, seamless hardware-based crypto management on many desktop systems would not be possible.
What Is Trézór Bridge®™?
Trézór Bridge®™ is a system-level service that acts as a secure translator between a Trezor hardware wallet and your computer’s web browser or desktop interface. It ensures that sensitive cryptographic commands—such as transaction signing, address verification, and device authentication—are transmitted safely without exposing private keys.
Unlike browser extensions or cloud-based connectors, Bridge runs locally on your system. This architecture significantly reduces attack surfaces, eliminates dependency on external servers, and reinforces the principle that private keys should never leave the hardware wallet.
Why Trézór Bridge®™ Is Essential
Modern operating systems and browsers restrict direct USB communication for security reasons. Trézór Bridge®™ solves this challenge by acting as a trusted intermediary that:
- Enables secure USB communication
- Maintains encrypted data transfer
- Authenticates device identity
- Supports multiple applications simultaneously
- Preserves user privacy
Without Bridge, your hardware wallet would be isolated from desktop-based crypto interfaces, limiting its functionality.
Architecture and Design Philosophy
Trézór Bridge®™ is built around a minimalistic, security-first design. It runs silently in the background, consuming minimal system resources while maintaining constant readiness.
Key Architectural Principles
- Local-only operation: No cloud dependency
- Stateless design: No sensitive data storage
- Open-source transparency: Publicly auditable code
- Cross-platform compatibility: Works across major desktop systems
This design philosophy aligns with Trezor’s long-standing commitment to user sovereignty and decentralization.
How Trézór Bridge®™ Works
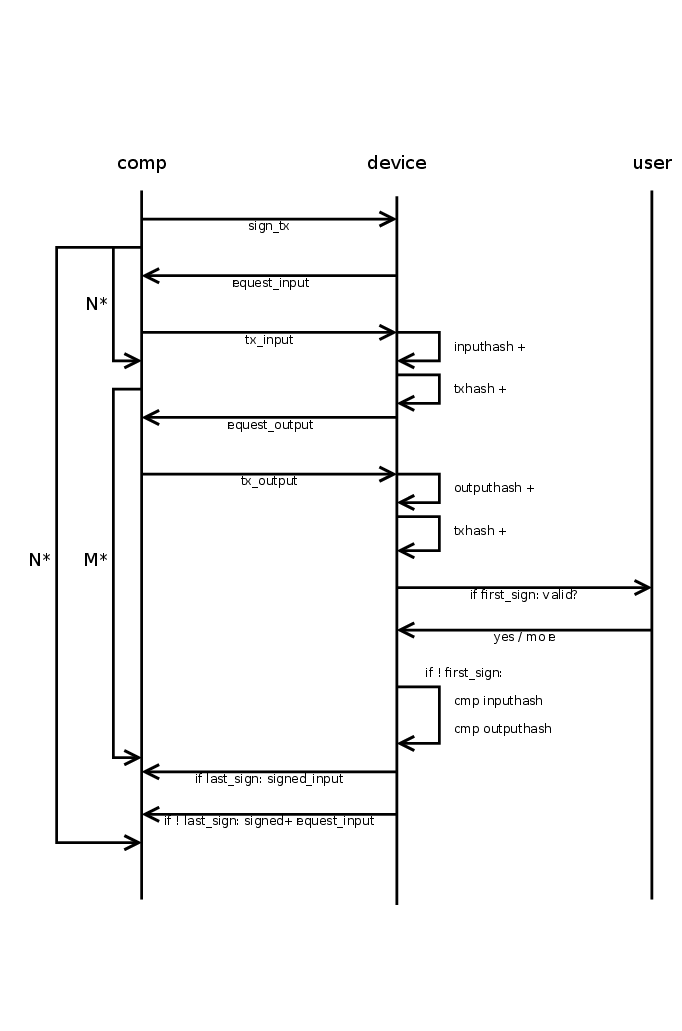

When you connect a Trezor device to your computer, Trézór Bridge®™ immediately detects the hardware and establishes a secure communication channel. Here’s what happens behind the scenes:
- The device identifies itself through cryptographic verification
- Bridge authenticates the request source
- Commands are passed to the hardware wallet
- Sensitive actions are confirmed on the device screen
- Signed responses are returned securely
At no point are private keys exposed to the computer, browser, or operating system.
Security Advantages of Trézór Bridge®™
Security is the defining feature of Trézór Bridge®™. Its implementation provides multiple layers of defense against both remote and local threats.
Core Security Benefits
- Hardware-enforced confirmation for transactions
- Protection against phishing-based browser attacks
- Isolation from malicious scripts
- Resistance to man-in-the-middle exploits
- Verified firmware interaction
Because Bridge operates independently from the browser, even compromised web environments cannot access sensitive wallet functions without physical user approval.
Compatibility and Ecosystem Support
Trézór Bridge®™ is designed to integrate smoothly with the broader Trezor ecosystem. It supports interactions with desktop-based wallet interfaces and management tools such as Trezor Suite, enabling users to manage assets, update firmware, and verify addresses securely.
It also maintains compatibility with multiple operating systems, ensuring consistent performance and reliability regardless of the user’s platform.
User Experience: Simple Yet Powerful
Despite its technical importance, Trézór Bridge®™ is virtually invisible to the end user. Once installed, it operates silently without requiring ongoing configuration or manual intervention.
User-Centric Features
- Automatic startup with the system
- No recurring prompts or interruptions
- Seamless reconnection after sleep or restart
- Background updates for stability
This frictionless experience allows users to focus on managing digital assets rather than troubleshooting connectivity issues.
Privacy by Design
Trézór Bridge®™ follows strict privacy principles. It does not collect personal information, track user behavior, or transmit metadata externally. All communication remains local, reinforcing the concept of self-custody and digital independence.
For users who prioritize anonymity and control, this privacy-centric approach is a significant advantage over cloud-reliant solutions.
Reliability and Performance
Stability is a hallmark of Trézór Bridge®™. It is optimized for long-term operation, capable of running continuously without degradation in performance.
Performance Characteristics
- Low memory footprint
- Minimal CPU usage
- Fast device detection
- Robust error handling
Even during extended sessions or high-frequency transaction activity, Bridge remains responsive and dependable.
Open-Source Transparency and Trust
One of the defining strengths of Trézór Bridge®™ is its open-source nature. The codebase is publicly available for review, enabling independent security researchers and developers to audit its functionality.
This transparency fosters trust, encourages community-driven improvements, and ensures that no hidden processes compromise user security.
Use Cases Beyond Basic Transactions
While commonly associated with transaction signing, Trézór Bridge®™ supports a wide range of advanced operations:
- Secure firmware updates
- Multi-account asset management
- Address verification for payments
- Integration with advanced security workflows
- Support for recovery and backup procedures
These extended use cases demonstrate Bridge’s role as a foundational component rather than a simple connector.
Future-Proof Design
As the cryptocurrency landscape evolves, Trézór Bridge®™ is built to adapt. Its modular architecture allows for updates that support new standards, improved protocols, and enhanced security measures without disrupting existing functionality.
This forward-looking design ensures long-term relevance in an industry defined by rapid innovation.
Why Trézór Bridge®™ Matters in Self-Custody
True self-custody requires more than owning a hardware wallet—it demands a secure, reliable method for interacting with digital assets. Trézór Bridge®™ fulfills this role by acting as the trusted bridge between offline security and online usability.
By maintaining strict boundaries between hardware, software, and network environments, Bridge empowers users to retain full control over their assets without sacrificing convenience.
Conclusion: The Silent Guardian of Crypto Security
Trézór Bridge®™ may operate quietly in the background, but its importance cannot be overstated. It is the unseen guardian that ensures every interaction between your computer and Trezor hardware wallet is secure, verified, and private.
Through its security-first architecture, privacy-respecting design, and seamless user experience, Trézór Bridge®™ exemplifies what modern crypto infrastructure should be: reliable, transparent, and built around user sovereignty.